
End-to-End Encrypted File Sharing System
UC Berkeley - Spring 2020

Overview
For my computer security class, I worked with a partner, Sachi Kulkarni, to design the backend of a stateless file sharing client in Golang with file storage, loading, sharing, and permission revocation functionalities. We utilized symmetric and public key encryption, digital signatures, HMACs, and hash functions along with a tree-based communication system to provide confidentiality, authenticity, and integrity for the client's users. We tested against a malicious data storage server and adversarial users, and protected against 80% of attacks. We worked on the project during March 2020, and we brainstormed, pair programmed, and tested over video chat since neither of us were in Berkeley due to the pandemic.
Threat Model
Our client had to be secure against two threats, a malicious data storage server and adversarial users. Since our client had to be stateless, our program's data had to be stored in the data storage server in order to be able to carry over to new sessions. The malicious server had access to all content, the time of entry, and who the entry came from for every data key-value pair stored in the server. On top of this, adversarial users could try to gain access to legitimate users' files or corrupt other files.
Example
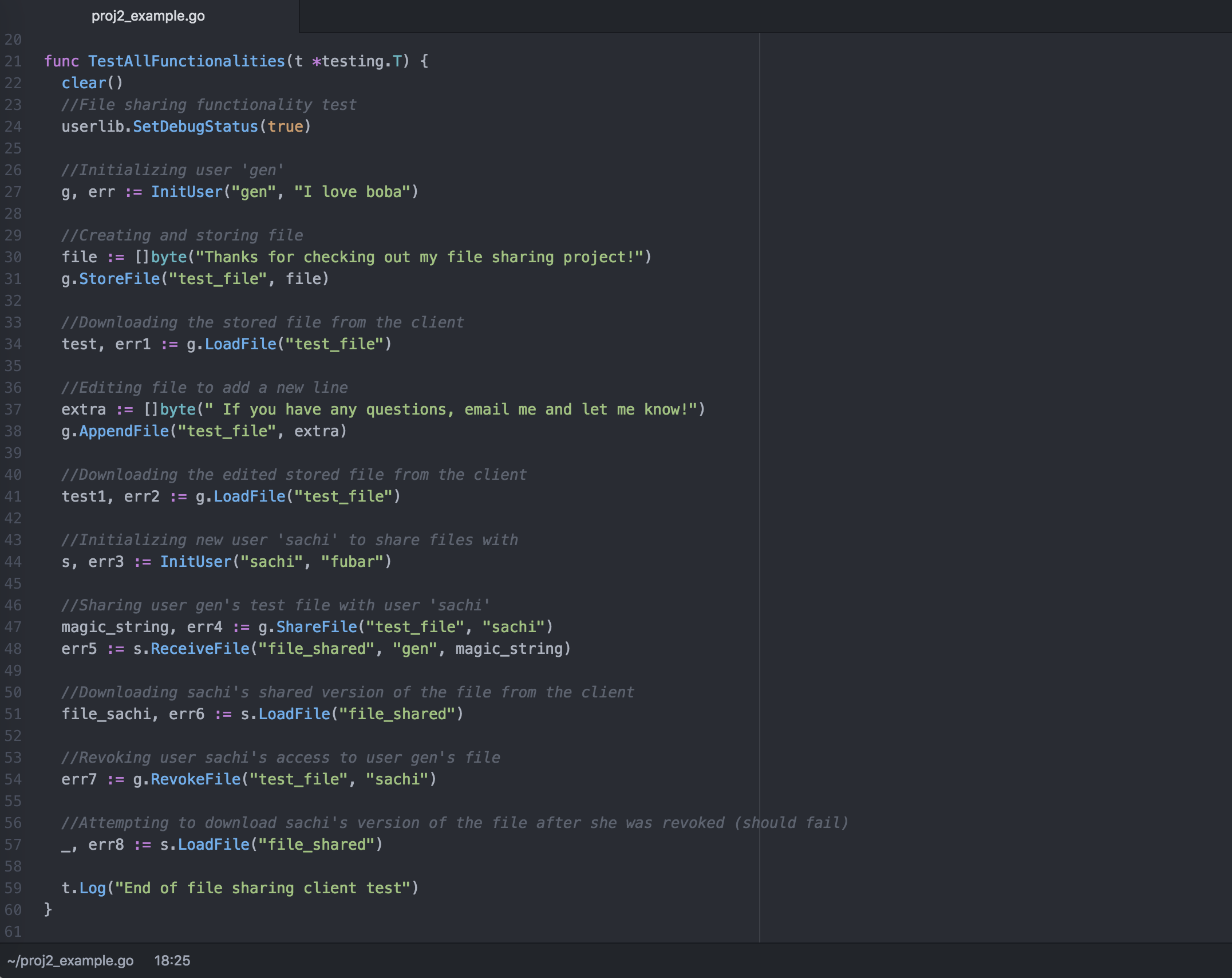
Shown above is an example of the functionalities of the file sharing client. In this interaction with the client, I will be initializing a user for myself with the username "gen" (and password "I love boba"), uploading and downloading a file, and editing the same file to add more content. Then I will create another user with username "sachi," share the original file with this user, and then revoke this user's access to the file.
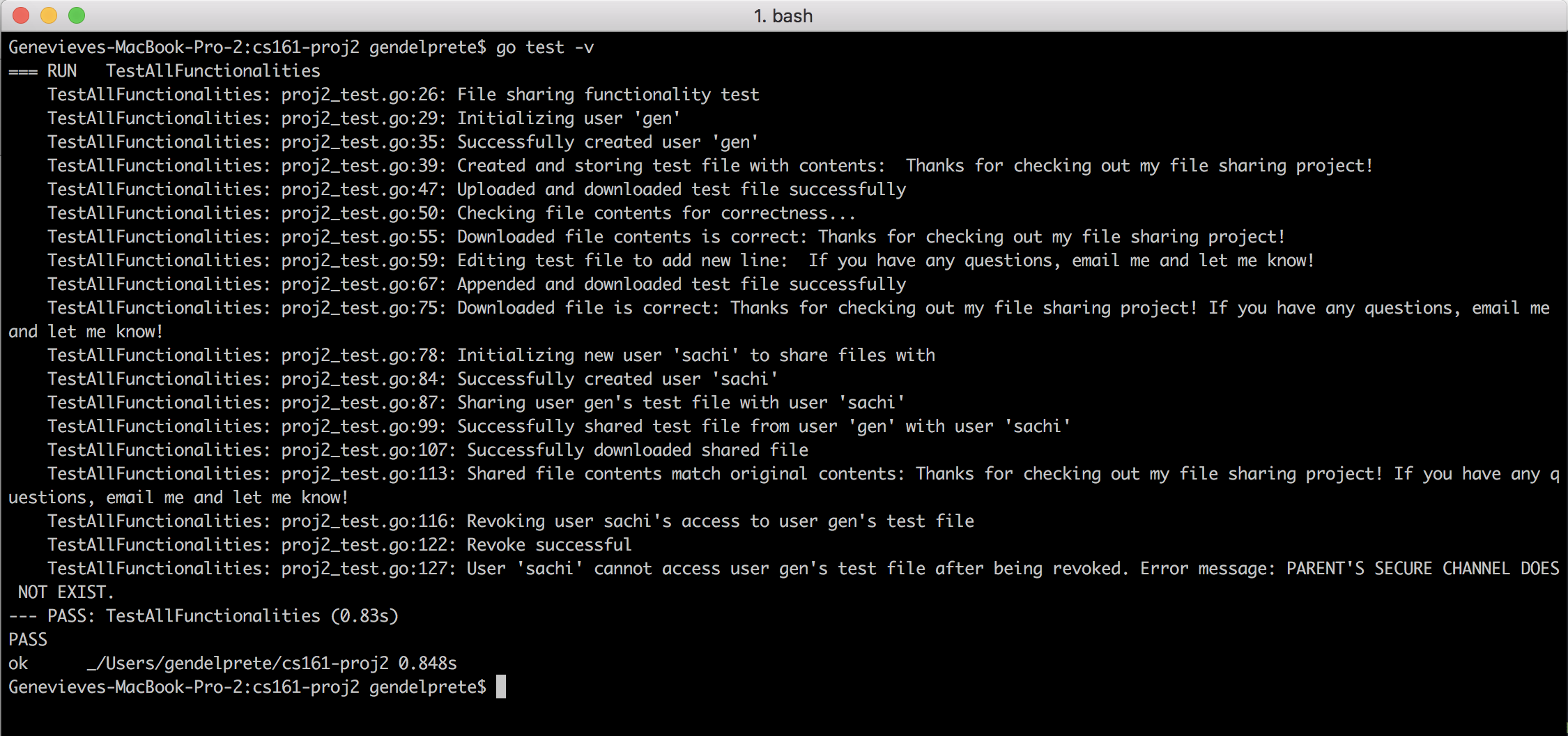
After adding error and logging statements to the test to see what was happening while the client is running (code not shown for clarity), I ran the test through the command line. The outcome is shown above. The client successfully stored, edited, and downloaded the test file, and also shared and revoked the other user's access to the file. Under the hood, multiple layers of encryption, decryption, and authentication signatures were applied to the users' credentials and the file's contents and metadata in order to protect all of the users' data against malicious users and the malicious data storage server where all of the client's data had to be stored.
Languages and Tools Used


To learn more about our design (which can't be shared online since the project is reused), please reach out to me at gendelprete@gmail.com!


